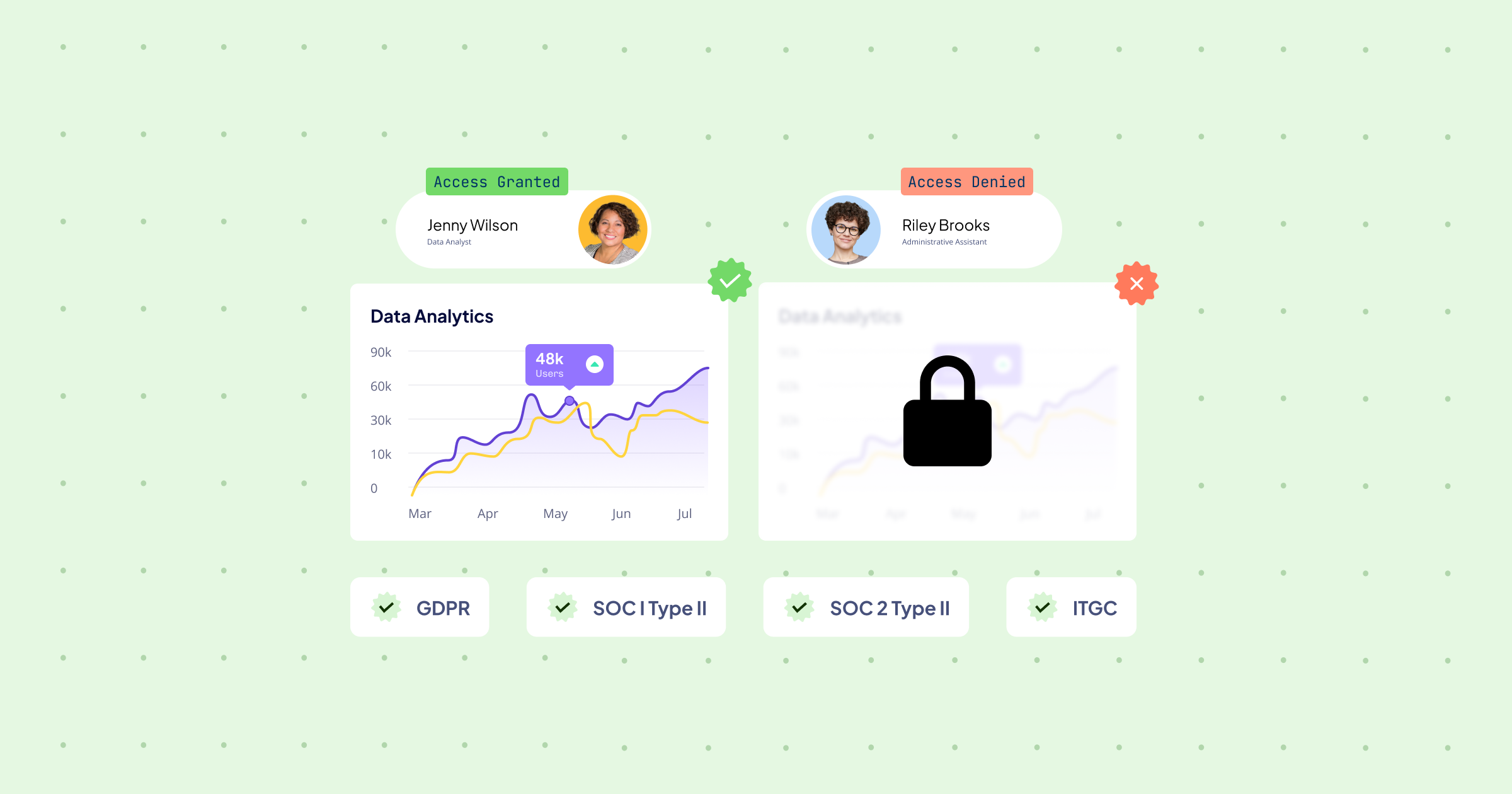
What is role-based access control?
Definition of role-based access control
Role-based access control (RBAC) is an authorization system designed to regulate access to systems and data by linking permissions directly to specific organizational roles. Unlike traditional access control methods that assign permissions to individual users, RBAC centralizes access management by associating permissions with defined roles within the organization. These roles are crafted to align with a user’s hierarchical position and departmental responsibilities, ensuring that access rights are tailored to the job function’s actual needs.
What are the key components of role-based access control?
Role-based access control is structured around several key components that work together to manage access control within an organization. These components include roles and data scoping. Here’s a breakdown of each:
Roles: Role-based access determines what areas of the application users have access to and what workflows they can perform (i.e., menus, buttons, and fields). Implementing role-based access control adheres to the principle of least privilege. This approach minimizes security risks by restricting access to sensitive data and functions that are not essential for their role.
Data scoping: Data scoping determines what specific data users can view (i.e., company codes and locations). By restricting access to only the data relevant to each user, data scoping improves security and ensures that sensitive information is protected from unauthorized viewership.
Usual role types and typical permissions
This table outlines the usual role types and their typical permissions within an organization, focusing on three key roles: Administrator, Manager, and Employee. Each role comes with distinct access levels and responsibilities, ensuring that the right users have appropriate permissions to perform their duties effectively.
| Roles | Administrator | Manager | Employee |
| Description | Administrators hold the highest level of access within the system. | Managers oversee specific departments or teams. | Employees perform specific operational tasks within their respective departments. |
| Typical Permissions | Full access to all system features, settings, and data, including user management and system configuration. | Access to departmental data, ability to approve or reject requests, generate reports, and manage subordinate user permissions. Limited access to broader system settings. | Restricted access to data and features relevant to their job functions, including data entry and task completion. |
With a clear structure of roles, data scoping, and permissions, RBAC helps organizations maintain security and operational efficiency. Now, let’s take a closer look at the specific benefits that RBAC brings to your company.
What are the top 5 benefits of role-based access control?
Role-based access control for enterprise-level applications offers significant advantages for organizations aiming to strengthen their security and streamline access management. In this section, we’ll explore the top five benefits of RBAC, including mitigation of insider threats, advanced protection against external breaches, minimized data loss, improved compliance and data integrity, and enhanced scalability and adaptability.
Mitigation of insider threats
Role-based access control enhances enterprise software security by enforcing the principle of least privilege, ensuring users receive only the access needed for their roles. This approach prevents “privilege creep,” where employees gain excessive access over time. Insider breaches, often linked to such excess access, make up 35% of data breaches, according to a Verizon report. By implementing role-based security, organizations can restrict unnecessary access and limit the potential for insider breaches.
Advanced protection against external breaches
Role-based access control is crucial for protecting against external breaches by limiting privileged accounts, which reduces the risk of unauthorized access to sensitive information. RBAC also supports the principle of segregation of duties (SoD), limiting the breach's scope to specific resources assigned to compromised accounts. This proactive defense is essential for large enterprises with stringent security requirements, especially those needing to comply with the Sarbanes-Oxley Act (SOX), which enforces SoD principles across information security standards.
Minimized data loss
While external attackers were responsible for 200 million records lost, internal breaches caused far greater damage, with over 1 billion records lost due to insider threats. Each internal attack exposed significantly more records than external attacks. Implementing strong role-based access control measures helps prevent such extensive data losses by ensuring that access to sensitive information is tightly controlled and monitored.
Improved compliance and data integrity
Maintaining compliance with data protection regulations, such as GDPR and SOC 1 and 2, is a critical concern for large enterprises, and role-based access control is instrumental in achieving this. By ensuring appropriate access controls, your enterprise can adhere to regulatory requirements and avoid hefty fines and legal repercussions.
Enhanced scalability and adaptability
As your organization grows, access management becomes more complex, requiring a flexible and scalable security approach. RBAC frameworks offer the adaptability needed to handle these changes by allowing easy updates to roles and permissions. This ensures smooth transitions as departments evolve and facilitates onboarding and offboarding by quickly assigning or revoking roles.
By following RBAC implementation best practices, organizations can fully realize the benefits of RBAC. Now, let's explore how Nakisa implements RBAC into its product portfolio to deliver these advantages in real-world applications.
How does Nakisa implement role-based access control in its product portfolios?
When it comes to safeguarding sensitive data and ensuring efficient access management and segregation of duties, implementing role-based access control is essential. Role-based security not only helps prevent insider threats but also ensures that only authorized users have access to critical information. Nakisa recognizes these security imperatives and has meticulously integrated RBAC into its products, ensuring that its portfolios—Nakisa Lease Accounting, Nakisa IWMS, and Nakisa Workforce Planning—are equipped to meet these demands.
How Nakisa implements RBAC in its software
Secure role-based access control with Nakisa is achieved through the Nakisa Cloud Platform, where all roles are assigned via single-sign-on (SSO). Our clients streamline user access by sending SAML files containing user roles, which are then mapped in cloud services to the preconfigured Nakisa software roles. This initial setup ensures that users are assigned the correct roles from the start.
For companies needing more detailed control, Nakisa Identity & Access Management (NIAM) can be integrated alongside SSO. This integration leverages secure, industry-leading practices such as standard SAML communication and renowned solutions like Keycloak.
NIAM simplifies the management of user provisioning and authentication to Nakisa’s solutions, ensuring that roles and profiles are accurately assigned. With customizable access privileges based on scope and duration, NIAM facilitates seamless user experiences for partners and employees across global subsidiaries while effectively controlling sensitive data access.
In addition, Nakisa’s role-based access control system allows for role stacking to ensure flexibility and comprehensiveness in access management. This means that users can be assigned multiple roles based on their specific access needs. Each user’s permission will be the cumulative sum of all their assigned roles, ensuring that they have the necessary access without unnecessary restrictions.
Nakisa’s commitment to security in RBAC
At Nakisa, ensuring the security and privacy of your data is our top priority. We undergo rigorous SOC 1 Type II and SOC 2 Type II audits annually, and we comply with GDPR requirements to ensure robust protection of your information. Our Nakisa enterprise-grade role-based access control features adhere to these requirements, enhancing the protection of your data. Learn more in our security page (for companies interested in obtaining certifications or reports related to our security practices, please complete this form to make your request).
Now, let's dive deeper into how RBAC is implemented across Nakisa's portfolios.
Role-based access control in Nakisa Lease Accounting
In Nakisa’s lease accounting software (AKA Nakisa Lease Administration or NLA), RBAC is crucial for regulating access to lease management and financial tasks. This system allows for the assignment of permissions necessary for handling lease agreements, financial records, and related activities. Data scoping is performed through User Profiles in the Financial Organization Structure (FOS) to ensure permissions are assigned appropriately, maintaining the integrity and confidentiality of data. In FOS, Authorization Profiles control user access to various application areas, with profiles that restrict visibility based on Lease Area, Business Unit, and Companies. It’s important to configure these profiles properly to prevent unauthorized access and ensure that users only see the data relevant to their roles.
Configuration of role-based access control in Nakisa Lease Accounting
Step 1: Configuring profiles and data access in the Financial Organization Structure
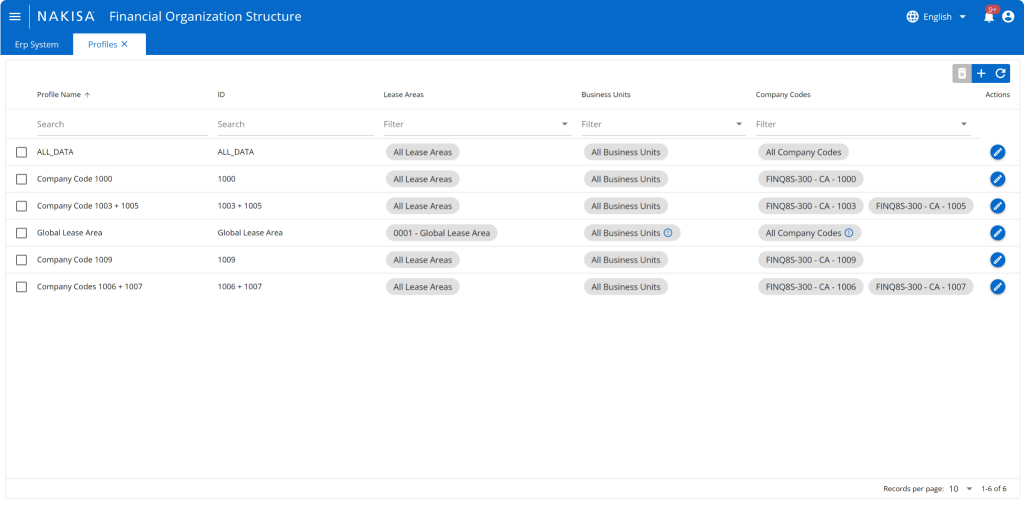
In this step, we configure profiles and select the data access permissions for each profile. This allows you to configure different profiles that restrict a user's access to data based on company code, lease area and business unit.
Examples:
- Profile name: ALL_DATA – Grants access to all lease areas, all business units, and all company codes.
- Profile name: Company Code 1003 + 1005 – Grants access to all lease areas and all business units but restricts access to company codes 1003 and 1005 only.
- Profile name: Global Lease Area – Grants access to the global lease area, all business units, and all company codes.
Step 2: Matching users with profiles in the Financial Organization Structure
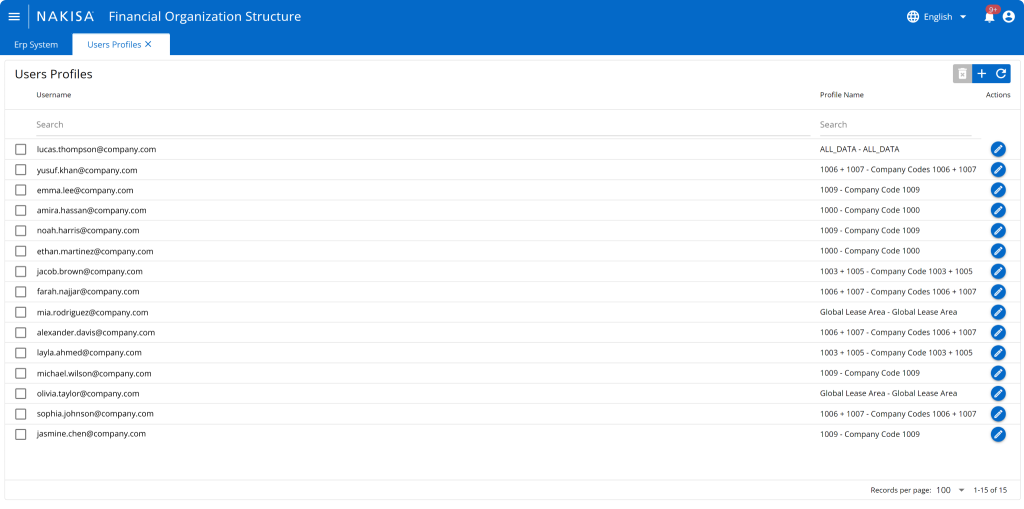
In this step, we assign profiles to users based on their access needs. Each user is matched with a profile to ensure they have the appropriate access to data.
Examples:
- The user lucas.thompson@company.com assigned the ALL_DATA profile will have access to all lease areas, business units, and company codes.
- Users jacob.brown@company.com and layla.ahmad@company.com with the Company Code 1003 + 1005 profile will have access to all lease areas and business units, but only company codes 1003 and 1005.
- The user olivia.taylor@company.com with the Global Lease Area profile will have access to the global lease area, all business units, and all company codes.
User role examples in Nakisa Lease Accounting
Nakisa’s lease accounting software features a range of user roles designed to manage and oversee lease-related financial tasks. Let’s delve into the main user roles in this portfolio and see how they facilitate effective management and compliance in lease accounting.
User role: Lease Administrator
| Role | Lease Administrator |
| Permissions | In Nakisa’s lease accounting software, Lease Administrators have the authority to create and manage master lease agreements, contracts, lease components, and activation groups. They handle tasks such as maintaining and activating activation groups, onboarding equipment, performing contract and activation group events, and executing mass lease modifications. They also update the status of posting documents and access management and certain compliance reports. |
| Use Case | Equipment onboarding and lease modifications A Lease Administrator needs to onboard new equipment for a recently signed lease. They create an activation group associated with Lease Component under Lease Contract and ensure that the activation group is properly activated in the system. They then execute mass modifications to adjust the terms of multiple leases and update the status of posting documents to reflect recent changes. |
User role: Accountant
| Role | Accountant |
| Permissions | Accountants can approve master lease agreements, as well as activate and classify activation groups. They can also generate different types of financial reports across periods—yearly, quarterly, and monthly. Additionally, they prepare and review compliance reports to ensure all financial entries and lease agreements meet regulatory and internal compliance requirements. |
| Use Case | Lease agreement approval and compliance reporting An Accountant needs to ensure accurate approval and compliance reporting for major office lease agreements. They approve a master lease agreement, then activate and classify the related activation groups. They also generate and review Balance Reports on lease agreements to ensure all financial entries are accurate and compliant with accounting standards such as IFRS 16 and ASC 842. |
User role: Reporting User
| Role | Reporting User |
| Permissions | Reporting users have access to all reports in Nakisa Lease Accounting. They can create, download, and view the available reports. The reporting user also has full access to the reports in the Nakisa SAP Posting Bot. |
| Use Case | Financial disclosure reporting A Reporting User is preparing the quarterly financial statements. They analyze data from all financial reports and the financial dashboard to provide insights into lease-related financial performance and position. They focus on ensuring that all disclosures are accurate and complete for regulatory compliance and internal review. |
Role-based access control in Nakisa IWMS
In Nakisa IWMS, RBAC controls access to a variety of facility management tasks. This includes managing permissions for users to handle operations related to facility maintenance, space management, and other key functions. Data scoping can be managed either through User Profiles in the Financial Organization Structure (FOS) or a combination of User Profiles and User Management for Nakisa IWMS users.
This approach ensures users have appropriate access for their responsibilities, improving operational efficiency and protecting sensitive workplace data.
Configuration of role-based access control in Nakisa IWMS
Extended access configurations in Nakisa IWMS
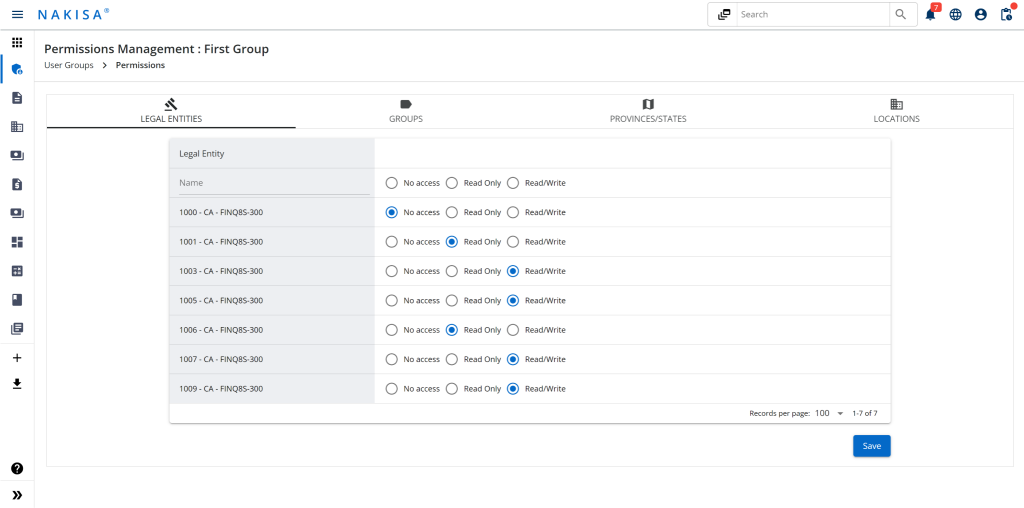
Similarly to Nakisa Lease Accounting, we also leverage the Financial Organization Structure for standard data access control for Nakisa IWMS. Additionally, Nakisa IWMS provides advanced configuration options through Permissions Management to tailor a user's access more precisely based on legal entities, groups, provinces/states, and locations.
User roles examples in Nakisa IWMS
Nakisa IWMS relies on role-based access control to manage secure access and streamline workflows related to real estate and workplace management. Let’s examine how RBAC is utilized within this portfolio to enhance access management and operational efficiency.
User role: Lease Administrator
| Role | Lease Administrator |
| Permissions | In Nakisa IWMS, Lease Administrators can create locations, premises, and contracts from the main menus, modify existing files, and run Financial Obligation Reports and CPI Mass Indexations. They also manage schedule payments and have access to the Nakisa SAP Posting Bot and Financial Organization Structure. |
| Use Case | Setting up store locations and managing financial obligations A Lease Administrator is tasked with setting up a new store location within the system, ensuring all details are accurately recorded. They then manage scheduled payments and generate a Financial Obligation Report to forecast future financial commitments. Additionally, they use the Nakisa SAP Posting Bot to integrate these obligations into the company’s financial records. |
User role: Manager
| Role | Manager |
| Permissions | Managers can access parts of the admin menu, including picklists and user-defined fields. They can create locations, premises, and contracts from the main menus and modify existing files. |
| Use Case | Manager oversight and configuration A Manager is tasked with setting up and overseeing office spaces within the system. They access the admin menu to configure settings in picklists and user-defined fields, ensuring that these elements are set up according to organizational standards. They create new locations, premises, and contracts, and make necessary modifications to existing records. The Manager also oversees these administrative functions, verifying that data entries are accurate, fields are properly configured, and the overall setup aligns with company policies. |
User role: Dashboard User
| Role | Dashboard User |
| Permissions | Dashboard users can access existing locations, premises, and contracts, and create and view custom and default dashboards. |
| Use Case | Monitoring and analyzing lease data A Dashboard User is responsible for monitoring and analyzing the company’s lease and real estate data to support strategic planning. They begin by accessing existing locations, premises, and contracts through the dashboard interface, gaining a full view of the company's assets and agreements. They then create custom dashboards tailored to specific metrics and KPIs, configuring widgets to display key data points and trends. |
Role-based access control in Nakisa Workforce Planning
In Nakisa’s workforce planning software, RBAC is strategically implemented to manage access to workforce-related information and planning tools. Each user role, from HR personnel to department managers, is assigned specific permissions to view, edit, or analyze data pertinent to their responsibilities. Data scoping is configured by Nakisa experts and performed by the Area of Responsibility to ensure precise access control.
User role examples in Nakisa Workforce Planning
In Nakisa’s workforce planning software, user roles are carefully defined to streamline and enhance the management of workforce data and planning processes. Let’s explore some of the key user roles within this portfolio and understand their distinct responsibilities and access privileges.
User role: Manager
| Role | Manager |
| Permissions | In Nakisa’s workforce planning software, Managers have access to various data, including specific data views, search capabilities (excluding secure fields), and the ability to update their own profiles. They also have access to dashboards for their areas and subordinates. Managers view high-level talent data for the entire organization but see detailed, secure data only for their direct reports. They can create org design proposals for their teams but do not have access to salary information outside their department. |
| Use Case | Team structure optimization A Manager is reorganizing their team for an upcoming project. They review dashboards to assess the current team structure and create an org design proposal for their team to suggest changes. They access specific data views to gather relevant information for their direct reports, ensuring that the proposed team structure aligns with departmental goals. |
User role: HR
| Role | HR |
| Permissions | HR users have access to all data and views in the application, both secure and non-secure, and can access all dashboards and analytics. They can create team design scenarios for the entire organization but cannot create org design or org merger scenarios. HR users can work in scenarios shared with them by Creators or Writers (defined below). |
| User Case | HR compliance and reporting An HR user is preparing a company-wide talent report for senior management. They access all available data and analytics to gain a complete view of the organization's talent distribution. They ensure that all data complies with company policies and collaborate with Creators on shared scenarios. Their objective is to deliver actionable insights in the report, such as assessing whether the scenario aligns with the span of control policy, remains within budget, and encompasses the number of organizational levels under their oversight. |
User role: Creator
| Role | Creator |
| Permissions | Creators can see all data visible to HR and can create org design and org merger scenarios for the entire organization. However, Creators cannot write finalized scenarios back to the HRIS. |
| Use Case | Org design and strategic alignment A Creator is an org design specialist responsible for developing a new organizational structure to support company initiatives such as mergers and acquisitions, reductions in force, or strategic realignments. They design and create org design and org merger scenarios to propose a revised organizational layout. They use their comprehensive access to ensure that these scenarios align with strategic goals. |
User role: Writer
| Role | Writer |
| Permissions | Writers can see everything that Creators can see and have the additional capability to write finalized scenarios back to the HRIS. |
| Use Case | Org design implementation in HRIS A Writer finalizes and writes back an org design scenario into the HRIS following a major organizational restructuring. They ensure that the finalized scenario is accurately recorded in the HRIS and reflects the updated organizational structure. |
Nakisa’s RBAC security features across its product portfolios ensure that access to sensitive data and critical features is meticulously controlled. By allowing for flexible role stacking and robust access management, Nakisa enhances data protection and compliance while tailoring access to meet the specific needs of each user.
Conclusion
Implementing role-based access control is essential for maintaining advanced security and operational efficiency in modern enterprises. By linking permissions to specific roles in enterprise software, the RBAC security model ensures that users have the appropriate level of access necessary for their job functions, adhering to the principle of least privilege. This not only improves data security and compliance with regulatory standards but also streamlines access management, reducing administrative overhead and mitigating security risks.
Leveraging RBAC in cloud-native solutions like Nakisa further enhances these benefits, as it integrates seamlessly with environments to provide scalable and dynamic access control tailored to evolving business needs.
Nakisa’s RBAC features across its product portfolios—Nakisa Lease Accounting, Nakisa IWMS, and Nakisa Workforce Planning —exemplifies the practical application of this security model. By defining user roles, assigning permissions, and configuring data scoping, Nakisa’s secure access management ensures that its solutions provide efficient, and compliant environments for organizational management, property management, and financial operations.
Take the next step towards securing your enterprise with Nakisa software access control, trusted by Fortune 1000. Contact us today to discover how Nakisa implements RBAC best practices in its comprehensive suite of products to enhance access control and optimize business operations.